Question:
What is the MAC address of the computer these files originated from?
(Hex in lower case)
Hint:
One of these files is the missing lnk to your answer.
Answer:
d0:50:99:82:33:6e
In
this challenge you were given a folder with random files I grabbed
from my computer. With these files, you should be able to deduce the
MAC address of my computer.
Only
one of these files is actually helpful to finding the answer. As the
hint hints, “One of these files is the missing lnk”. In Windows,
shortcut files contain a large amount of metadata of the original
file these link from, as well as the host computer. Magnet Forensics
has a short article explaining some information about LNK files here:
https://www.magnetforensics.com/computer-forensics/forensic-analysis-of-lnk-files/.
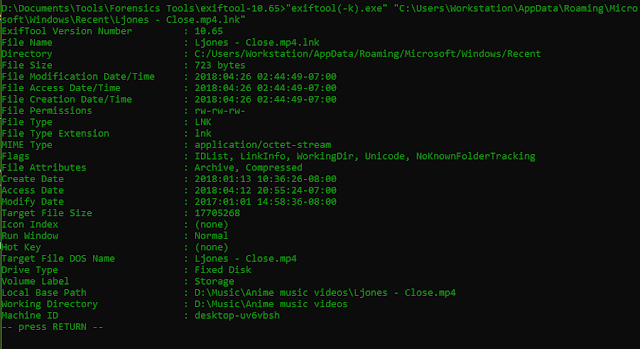
Exiftool is a great tool for find information and metadata about
files. Using Exiftool on “Ljones – Close.mp4” gives the
following results:
A
lot of information came from such a small file! We can see
interesting data such as Volume Label, Machine ID, Target File Size
and more. Unfortunately Exiftool did not find the MAC address.
Exiftool works best for finding Exif metadata. For the forensic
analysis of LNK files, Eric Zimmerman’s Link Explorer works great.
You download Link Explorer (LECmd) from
https://ericzimmerman.github.io/.
To
specify a file to examine, use the “f” flag:
LECmd.exe
-f “Ljones – Close.mp4.lnk”
This
displays a lot of additional information compared to Exiftool.
Scrolling down we can see in addition to the Machine ID that we found
earlier, we have discovered the MAC address: d0:50:99:82:33:6e. Next
time you do your forensic investigation, be sure to check out any
link files on Windows machines.
Like my work? Donate here: https://buymeacoffee.com/forensicnoobsecurity