Sunday, December 1, 2019
Finding the Last Logon - Cal Poly FAST CTF Challenge 14
Question: What was the timestamp when Patrick last logged off? FORMAT: M/DD/YYYY H:MM:SS
Points: 70
Download File from: https://github.com/mfput/CTF-Questions/raw/master/Security
Hint: No Hint
Answer: 4/10/2017 6:32:00
Finding Interactive Logons - Windows Event Logs - Cal Poly FAST Challenge 13
Forensic Challenge 13:
Question: How many interactive logons were there on this machine?
Points: 100
Download File from: https://github.com/mfput/CTF-Questions/raw/master/Security
Hint: There are multiple types of logons.
Answer: 23
This is the first of three questions centered around the Windows Security event log. The file is an EVTX Windows event log from a Windows 7 machine. The extension has been removed, so you'll have to add the .evtx extension. You'd have to use the file command to figure out it is a event log file. I will be showing how to solve these 3 Windows event log questions with the native Event Viewer, of course you could also ingest the .evtx file into a supported program with better query functionality.
You can natively open this file with the Event Viewer. Once opened, it can be quiet overwhelming seeing all these logs. Of course, we are looking for something in particular, the number of interactive logins. Each event is group by a Windows event ID. The standard Windows event ID for account logins is 4624 "An Account was successfully logged on". We can filter the Windows event log by pressing the "Filter Current Log" on the right panel, and entering the 4624 event ID.
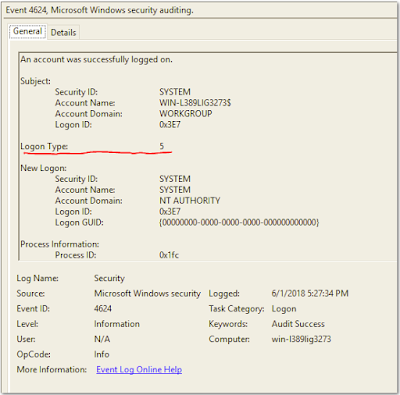
Once we have this log filtered, we can see that there 279 events from ID 4624. However, not all were an actual interactive login. When we select the individual event, we can see the details and see a field called "Logon Type":
There are multiple types of logins, which we are only interested in one. In the above log we see a Logon Type of 5, which is a Service logon. We want to filter by type 2, interactive logons. Below is a list of the different logon types available:
Logon Type
Description
2 Interactive (logon at keyboard and screen of system) 3 Network (i.e. connection to shared folder on this computer from elsewhere on network) 4 Batch (i.e. scheduled task) 5 Service (Service startup) 7 Unlock (i.e. unnattended workstation with password protected screen saver) 8 NetworkCleartext (Logon with credentials sent in the clear text. Most often indicates a logon to IIS with "basic authentication") See this article for more information. 9 NewCredentials such as with RunAs or mapping a network drive with alternate credentials. This logon type does not seem to show up in any events. If you want to track users attempting to logon with alternate credentials see 4648. MS says "A caller cloned its current token and specified new credentials for outbound connections. The new logon session has the same local identity, but uses different credentials for other network connections." 10 RemoteInteractive (Terminal Services, Remote Desktop or Remote Assistance) 11 CachedInteractive (logon with cached domain credentials such as when logging on to a laptop when away from the network)
Source: https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventID=4624
NOTE: Interactive logins can come from other Event IDs as well, but are not present in this event log.
We want to filter by the interactive logon type of 2. Alas, this isn't possible with the simple click of a button in the Event Viewer, but it is possible using XPath. All Windows event logs are written in XML, and each attribute is an XML entity which we can query. From a selected event log, we can choose "Details -> XML View". With this, we can see the Data Name which we will use to query, "LogonType".
Go to the "Filter Current Log" on the right hand pane, switch to the XML tab, and press "Edit query manually". This will allow us to right custom XPath queries to gather more specific data. Because this is a saved log, the Path will be different from mine. After the Select Path asterisk, replace
[System[(EventID=4624)]] NOTE: This queries the Sytem entity for an Event ID of 4624.
with:
[EventData[Data[@Name='LogonType']='2']] NOTE: This queries the Event Data entity for a logon type of 2. The event Data is independent of the System entity, meaning if there are an other event IDs that have this event data, they will also appear.
With this, we can see that there were only 23 actual interactive logons in this event file.
There are multiple types of logins, which we are only interested in one. In the above log we see a Logon Type of 5, which is a Service logon. We want to filter by type 2, interactive logons. Below is a list of the different logon types available:
Logon Type
|
Description
|
| 2 | Interactive (logon at keyboard and screen of system) |
| 3 | Network (i.e. connection to shared folder on this computer from elsewhere on network) |
| 4 | Batch (i.e. scheduled task) |
| 5 | Service (Service startup) |
| 7 | Unlock (i.e. unnattended workstation with password protected screen saver) |
| 8 | NetworkCleartext (Logon with credentials sent in the clear text. Most often indicates a logon to IIS with "basic authentication") See this article for more information. |
| 9 | NewCredentials such as with RunAs or mapping a network drive with alternate credentials. This logon type does not seem to show up in any events. If you want to track users attempting to logon with alternate credentials see 4648. MS says "A caller cloned its current token and specified new credentials for outbound connections. The new logon session has the same local identity, but uses different credentials for other network connections." |
| 10 | RemoteInteractive (Terminal Services, Remote Desktop or Remote Assistance) |
| 11 | CachedInteractive (logon with cached domain credentials such as when logging on to a laptop when away from the network) |
Source: https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventID=4624
NOTE: Interactive logins can come from other Event IDs as well, but are not present in this event log.
[System[(EventID=4624)]] NOTE: This queries the Sytem entity for an Event ID of 4624.
with:
[EventData[Data[@Name='LogonType']='2']] NOTE: This queries the Event Data entity for a logon type of 2. The event Data is independent of the System entity, meaning if there are an other event IDs that have this event data, they will also appear.
With this, we can see that there were only 23 actual interactive logons in this event file.
Subscribe to:
Posts (Atom)